
Emails allegedly sent on behalf of Ukrtelecom contained files that launched a spyware program, reports the Government Computer Emergency Response Team of Ukraine CERT-UA.

E-mails with the subject “Court claim against your personal account # 7192206443063763 dated: 06.02.2023” and an attachment in the form of a RAR archive “court letter, information about debt.rar” were received on the computers of employees of state authorities of Ukraine. The attachment contained a text document and another password-protected archive with an embedded file “court letter, debt information.pdf.exe” over 600 MB in size.
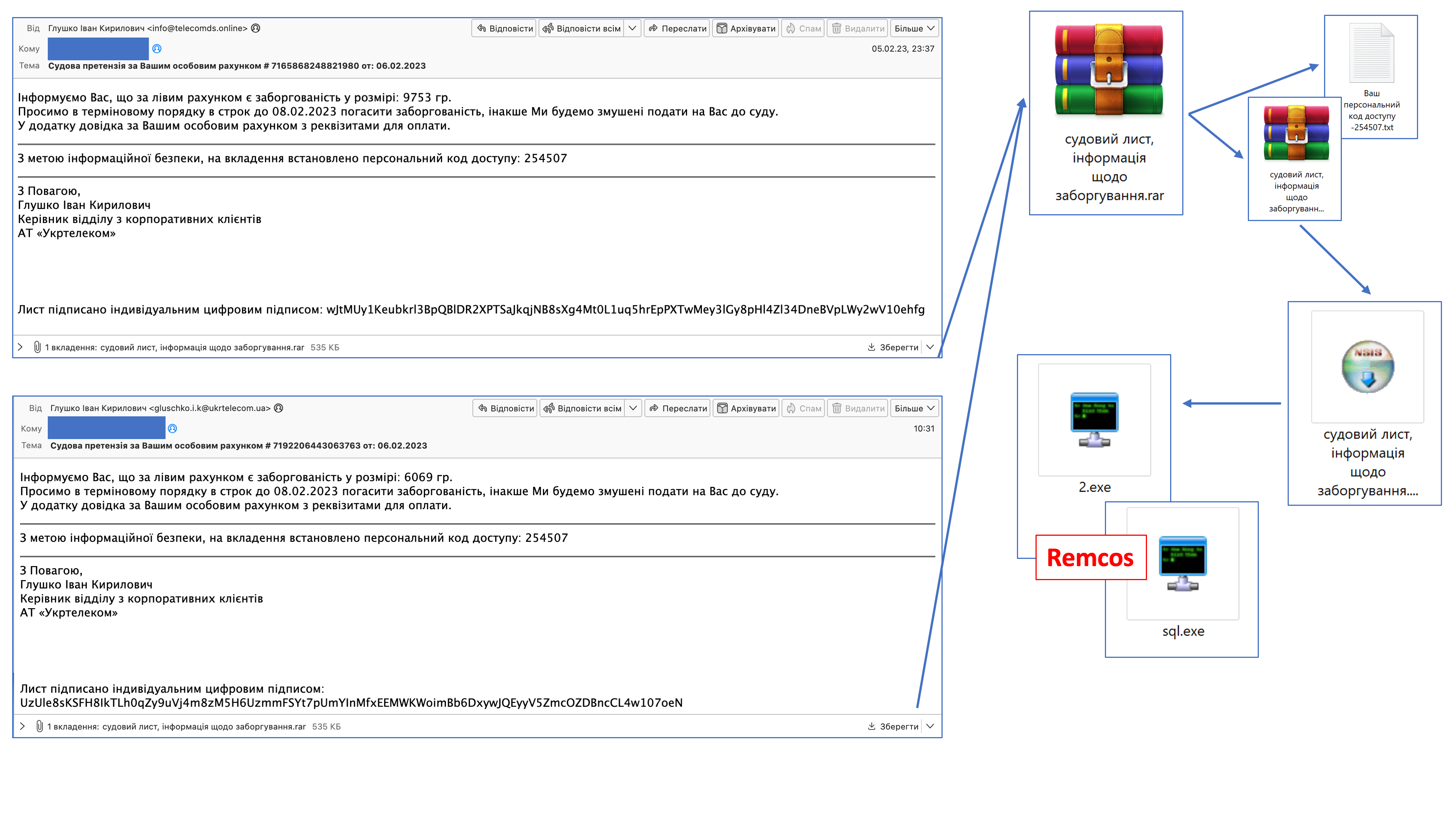
When the file was launched, Remcos – a program for remote monitoring and surveillance from the BreakingSecurity company – was installed on the computer. It is usually used for legitimate remote administration, but in this case the hackers planned to spy on the victims’ computers.
Tame Power BI and predict the future of your company.
REGISTER!
“The detected activity has been tracked under UAC-0050 since at least 2020. Previous cyberattacks were carried out using the RemoteUtilities remote administration program. Based on the functionality of the programs and the fact that the objects of cyberattacks are usually the state authorities of Ukraine, it is considered that the attack is carried out for the purpose of espionage,” says CERT-UA.
Previously, cybercriminals already tried to steal data, masquerading as the Ministry of Foreign Affairs of Ukraine, as well as the State Emergency Service (using the theme of Iranian Shahed-136 kamikaze drones). In October-November 2022, similar letters also allegedly came from the State Special Communications, the press service of the General Staff of the Armed Forces of Ukraine, the Security Service of Ukraine, and from CERT-UA.
The developer pretended to be a hacker and demanded $2 million in cryptocurrency from his own company — he was exposed due to a VPN malfunction




